For computer security, enforcing the principle “do not let your left hand know what your right hand is doing” is vital.
Modern computers and smartphones do many things at the same time. For example, you may have a browser with one tab playing a song while in another you are logged into your bank account, paying a bill with a QR code that you scan with your camera. Under no circumstances should the audio player’s tab be able to use the privileges that you have granted to the banking tab. These privileges include access to your camera and access to your bank account, so long as you are logged in. With that level of access the audio player could access your bank account and issue illicit transactions. In this example the browser is a single program handling multiple tasks at the same time. If all tasks run in the same isolation domain then any bug in any task would allow the abuse of the privileges of all other tasks. Each task (and their privileges) must therefore be kept separate and isolated from all others.
Today, the only viable solution is process isolation. Each task runs in an independent process with tight limits on how it can interact with the operating system. This interface, born in the 80s, takes tens of microseconds to switch between any two tasks. Compared to the 80s, today’s programs are many orders of magnitude more complex. A browser consists of around 100 million lines of code (printed on A4 paper, the stack of source code would reach 400m). Given the high switching cost between processes, this isolation is limited to coarse-grained tasks such as individual browser tabs. Instead, it would be better to isolate fine-grained tasks such as restricting an ad or social media interaction from the main web page that is displayed, or to isolate the library that scans your QR code from the rest of the banking app.
Researchers at Prof. Mathias Payer’s HexHive Lab, in collaboration with Prof. Babak Falsafi’s PARSA Lab, have come up with a surprising approach to this problem, achieving fine-grained isolation of sub-tasks in nanoseconds, thereby providing much tighter security guarantees at low performance cost.
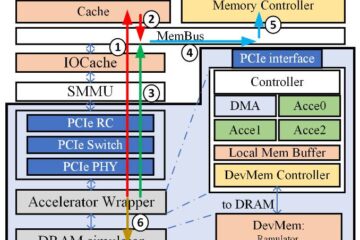
On a computer, each program runs in a so-called virtual address space, a flat array of memory where all code and data is stored. SecureCells, like its related project Midgard, supercharges the address space, and repurposes it: in this case, for compartmentalization. Traditionally, all sub-tasks have access to all code and all data. SecureCells uses compartmentalization to break up the address space into logical compartments which enforce isolation between each one. Code from one compartment can only access data it is given access to.
Compartmentalization works at a finer level than traditional process isolation. First conceived in the 1980s, it is a principle by which software is broken into clearly defined and differentiated areas of memory: compartments, which are separated from each other. Originally, compartmentalization worked by separating address spaces and running each process in its own address space. Separating address spaces is costly and switching between them takes time, in the order of microseconds. Instead, the researchers at HexHive are breaking a single address space into compartments and enforcing security checks at compartment transitions, not address space transitions.
“SecureCells is designed as a secure mechanism inside a single address space, you don’t have to switch address spaces, saving valuable time” explains Prof. Payer. “All the architectural and microarchitectural costs of switching are dispensed with. Switching compartments takes place at the nanosecond scale, with very little overhead.”
The results are dazzling. Using the address space in this new way drastically reduces the cost of compartmentalization while guaranteeing security properties.
Doctoral Assistant Atri Bhattacharyya, who is jointly advised by Mathias Payer and Babak Falsafi, is clear about this: “SecureCells is a secure mechanism on which to build secure applications. It is a mechanism with an isolation guarantee, and prohibits privilege escalation. We base our guarantee against privilege escalation, with checks implemented for each unprivileged operation in our mechanism.”
Industry players have also attempted compartmentalization, with varying degrees of success, according to Bhattacharyya. “Arm and Intel are trying similar techniques. Intel’s MPK is a step in this direction, but lacks strong security properties for code. There is a general push in this area, across industry and academia.”
“Qualcomm and Intel have both shown an interest in SecureCells,” according to Prof. Payer. “With today’s complex software we need to find ways to break software into small compartments, enforcing security guarantees between each one. Taking a large address space and dividing it into smaller pieces, with architectural extensions to allow data to go back and forth much faster – this is the best answer to this complex problem.”
And where did the idea come from? “Three years of tracking upcoming problems in the security space, noticing common patterns, and defining the challenge. With a well-defined problem statement, the solution just emerges from the problem,” explains Bhattacharyya. Which goes to show that three years of thinking can achieve amazing things: if it is the right people, in the right lab.
Paper: SecureCells: A Secure Compartmentalized Architecture
Website: Hexhive SecureCells
Interview: John Maxwell
Images: Alex Widerski